Cloud
Validation using policy as code
Enterprises leverage cloud computing to scale their applications and keep up with market trends. Cloud management is no longer the sole responsibility of a central admin team. Developers, testers, and other stakeholders are also involved. However, the decentralized and distributed nature of IT environments makes it difficult to implement and manage policies at scale.
Policy as code (PaC) automates the implementation of organizational policies at scale and manages alerts for any kind of non-compliance or policy breach in production or pre-production environments.
In this paper, we look at PaC from the purview of cloud computing.
What is PaC?
Cloud resources and services must adhere to a certain set of rules (in short, policy) that meet enterprise mandates for security, compliance, governance, etc.
While infrastructure as code (IaC) evolved to provision cloud environment at scale, PaC emerged to enforce enterprise-level policies at scale using a declarative programming language. PaC defines and manages policies using few lines of code in programming languages such as Python, Rego, and YAML. PaC can be enforced across the board before deployment and regularly evaluated thereafter. Codification helps to implement organizational standards and compliances at scale.
Here are some examples:
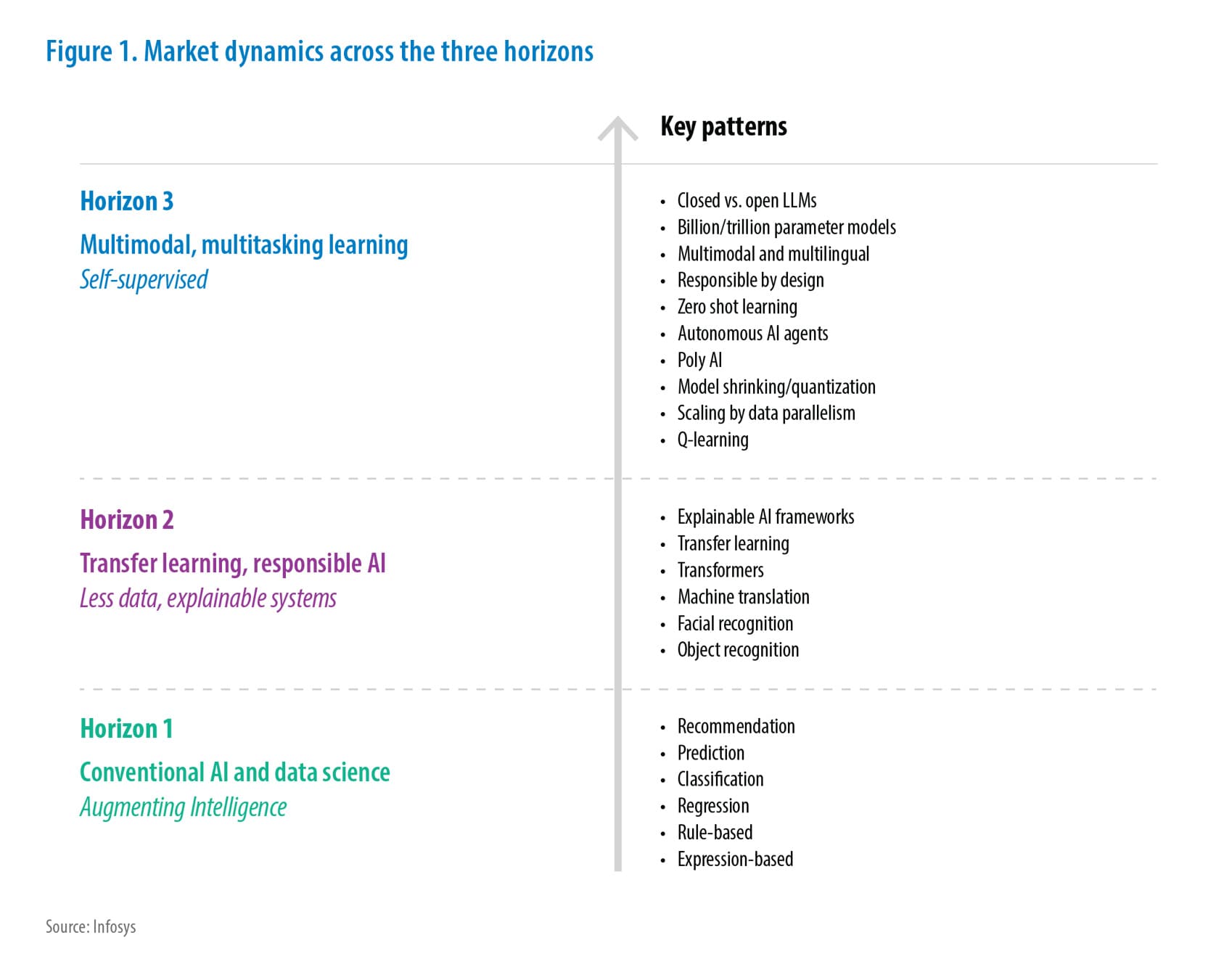
A policy written in JSON format that can be used with AWS Config Rules to check for encryption of sensitive data at rest on Amazon S3 :
Example 1 – Enforce S3 encryption
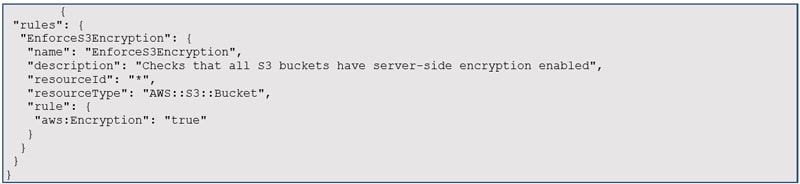
Rego code for EKS cost optimization policy
Example 2 – EKS cost optimization policy
Precisely, PaC is a set of reusable codes that can be embedded in the development pipeline.
Need for PaC
Earlier, a governance team or a centralized operations team used to review a policy document before approving or denying its enforcement. However, this approach can create delays and human errors in a distributed cloud environment. PaC validations can address these challenges. The policies should be applied at scale across multiple accounts with one cloud service provider (CSP) or a multicloud environment.
In a microservices-based application, tightly coupled policies make it difficult to modify or add policies after deployment. A separate policy repository with features like add, update, test, and deploy is necessary for large application portfolios.
At an enterprise level, we can create a policy repository in the form of a policy engine comprising policies across:
- Security
- Compliance
- Cost controls
- Governance
- Best practices
Enterprises need a comprehensive policy repository to store custom policies for their applications and environments. This engine will help enterprises fetch and amend policies from the repository before embedding them in the development pipeline.
The biggest challenge for cloud admins is to write policy scripts, which requires programming skills. However, there are open-source and cloud-native tools that write policy scripts by using programming languages, such as Python, Yaml, and Rego.
The varying APIs, services, and syntax for defining policies across cloud providers make it challenging to build a portable policy. We can use a combination of the below approaches to define and manage policies in a multicloud environment.
- Cloud agnostic policy language: A cloud agnostic policy language such as OPA (Rego) creates consistent policies across any environment, at any enforcement point (be it cloud infrastructure, Kubernetes, microservice APIs, databases, service meshes, or application authorization). This shortens the approach toward defining and enforcing policies across multicloud and hybrid cloud environments. Developers can use OPA to validate Terraform changes before they are provisioned in production. This ensures that the cloud environment meets the desired configuration.
- Configuration management tool: Terraform and Ansible define and enforce policies across cloud environments and support multiple cloud environments.
- Infrastructure abstraction layer: Crossplane and Cloud Custodian abstract differences between multiple cloud providers and define policies in a cloud-agnostic way.
- Policy management platform: A central policy management platform to manage all policy-related tasks and workflows across services in a multicloud environment is going to play a crucial role.
- Containerized approach: Docker and Kubernetes define policies for containers and deploy applications across multiple cloud providers and Kubernetes distributions. OPA can run on top of Kubernetes, so it is portable as well.
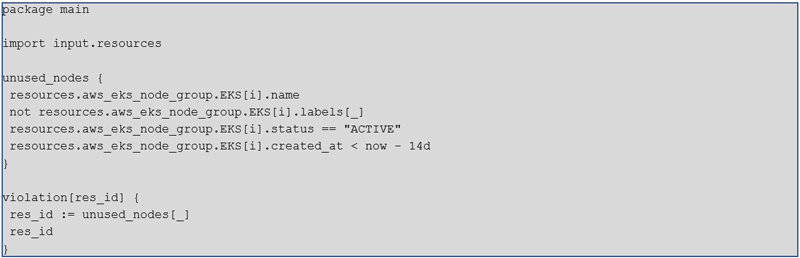
We can use OPA/Rego code to control Kubernetes ingress and egress decisions. This code can prohibit ingresses with conflicting hostnames. Below is an example code snippet:
Example 3 – Kubernetes ingress and egress decisions
An overview of which cloud services a policy applies to, and which cloud accounts should be included, is essential.
The system should generate a comprehensive report (with one click), comprising all cloud accounts, cloud services, and policy non-compliances.
For this, essential elements are:
- Apply cloud asset discovery to apply policies at scale and flag those cloud services and resources where a typical policy has not been applied.
- Have an agent that polls for areas where policies can be applied.
- Instrument policy scheduler to execute policy test cases at frequent intervals and evaluate policies based on the cloud services subscribed by the account(s), highlighting any non-compliance issues.
- Implement auto remediation for policy violations in most cases based on approval workflow.
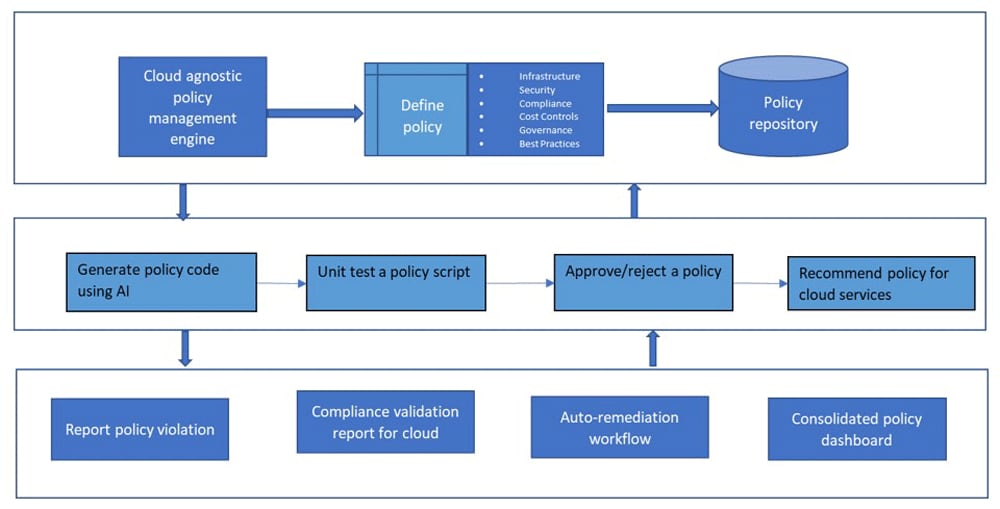
Architecture – Validation using PaC
The architecture of validation using PaC typically involves:
- Policy repository: A version control system such as Git to store all policies.
- Policy engine: It interprets and executes the policies stored in the policy repository. It is integrated with a continuous integration/continuous deployment (CI/CD) pipeline to automatically enforce PaC.
- Compliance scanner: It scans the infrastructure and applications to detect policy violations. It may use APIs or agents to collect data from the infrastructure and applications and report any violations to the policy engine.
- Policy dashboard: It provides a user interface to view policy status and violations and accordingly take actions.
- Remediation tool: It takes action to remediate policy violations. It can automatically fix issues or trigger a manual review process.
- Auditing and reporting: This process records all policy violations, remediation actions, and other events related to policy enforcement. This information can be used for auditing and reporting purposes.
- Policy management interface: It allows the policy management team to create, update, and delete policies.
- API gateway: It allows different modules of the architecture to communicate with each other.
- Policy recommendation: The system recommends a list of policies that should be applied when you create an object or cloud resource or subscribe to a cloud service.
Generative AI can be used to write Rego code for Open Policy Agent to identify security violations. For example, you can write a prompt to generate code that detects encryption in S3 buckets and restricts public access.
Example 4 – Detect encryption in S3 bucket and restrict public access
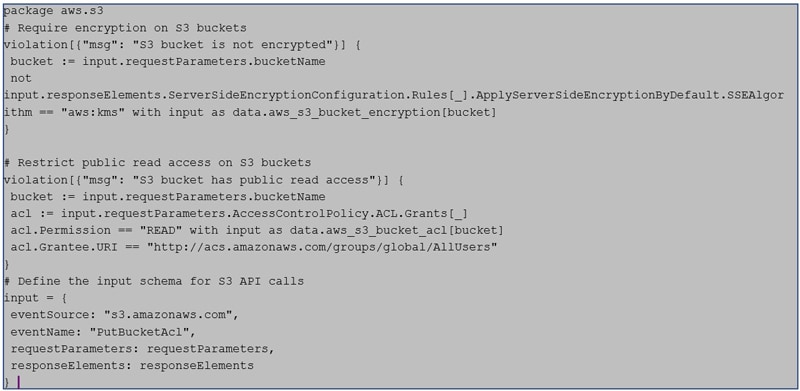
Figure 1: Prototype of validation using PaC
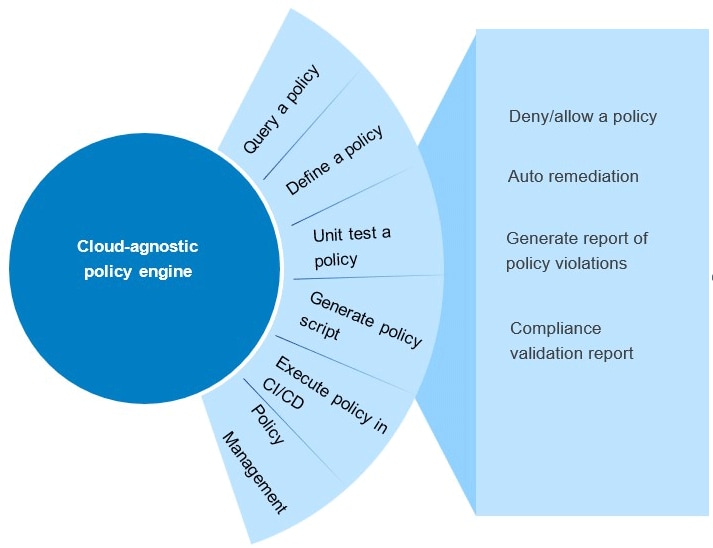
Figure 2: Typical architecture for validation using policy as code
As organizations migrate to the cloud, we need to provide a platform that can manage policies across multiple cloud accounts and hybrid cloud environments. We also need to provide out-of-the-box solutions using the latest technology stack, such as Generative AI.
References
- https://www.styra.com/blog/what-is-policy-as-code-definition-and-benefits/#:~:text=Policy%20as%20code%20provides%20an,wide%20and%20application%2Dlevel%20policies
- https://www.harness.io/blog/policy-as-code
- https://aws.amazon.com/blogs/opensource/cloud-governance-and-compliance-on-aws-with-policy-as-code/
- https://github.com/aws-samples/policy-as-code
Author
Abhinav Srivastava
Senior Technology Architect, ICETS,
Infosys

Subscribe
To keep yourself updated on the latest technology and industry trends subscribe to the Infosys Knowledge Institute's publications
Count me in!