Cybersecurity
Cybersecurity manages business risks throughout the value chain through processes, policies, and governance methodologies. The technology identifies, detects, protects, responds to, recovers from, and governs against cyber threats. It secures an organization's entire attack surface — cloud, workplace, IoT/OT, applications, big data, and AI models.
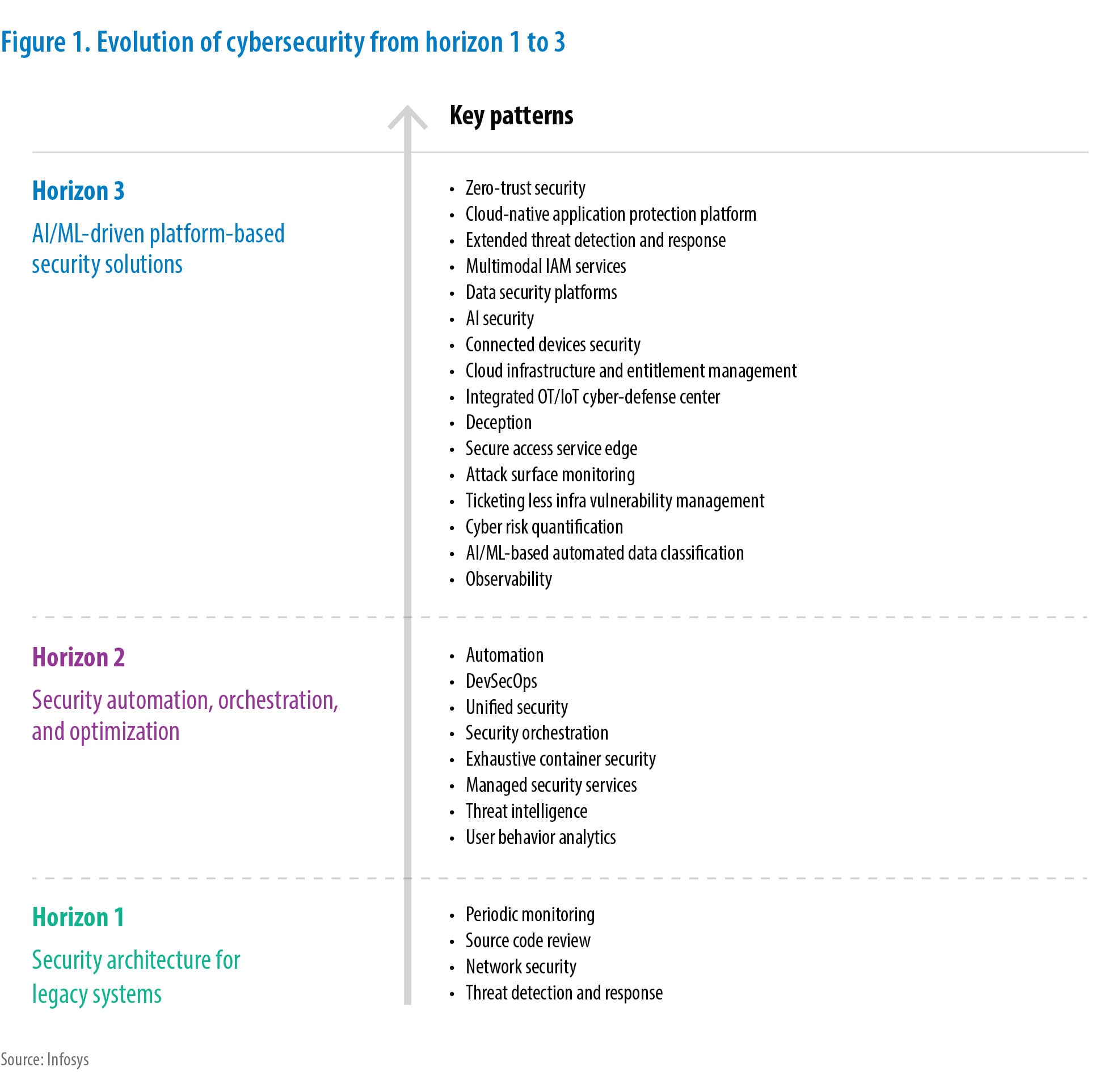
Cybersecurity's evolution to counter attacks
H3
AI/ML-driven platform-based security solutions
Key Patterns
- Zero-trust security
- Cloud-native application protection platform
- Extended threat detection and response
- Multimodal IAM services
- Data security platforms
- AI security
- Connected devices security
- Cloud infrastructure and entitlement management
- Integrated OT/IoT cyber-defense center
- Deception
- Secure access service edge
- Attack surface monitoring
- Ticketing less infra vulnerability management
- Cyber risk quantification
- AI/ML-based automated data classification
- Observability
H2
Security automation, orchestration, and optimization
Key Patterns
- Automation
- DevSecOps
- Unified security
- Security orchestration
- Exhaustive container security
- Managed security services
- Threat intelligence
- User behavior analytics
H1
Security architecture for legacy systems
Key Patterns
- Periodic monitoring
- Source code review
- Network security
- Threat detection and response
Key trends across cybersecurity subdomains
Trend 1
Developments in microsegmentation enable zero-trust alignment
Microsegmentation, once error-prone and disruptive, has evolved to become more focused and ROI-driven through modern advancements.
Trend 2
Proactive decoys and lures gain prominence for advanced cybersecurity and zero trust
Proactive lures and decoys, as part of deterring security control, will soon become a technology must-have. This cutting-edge technology possesses the ability to comprehend threat patterns and mimic attacker behaviors, offering a robust defense mechanism.
Trend 3
Advanced threat detection capabilities strengthen security measures in identity management
Advanced AI assists and improvises the user behavior detection process by analyzing and profiling patterns and responding to threats. Organizations integrate tools and processes, evaluate existing tools aligned with ITDR architecture, and incrementally deploy zero-trust capabilities to enhance ITDR.
Trend 4
Verifiable credentials/decentralized identity and passwordless authentication strengthen digital identity ecosystem security
The zero-trust model maintains that all users or devices, irrespective of their access location, are authenticated and authorized to access requested applications or services.
Trend 5
Data security platforms become a necessity to safeguard information
Organizations increasingly prioritize data protection from unauthorized access, use, disclosure, disruption, modification, and destruction. Higher data volumes, more cyberattacks, and stricter data protection regulations drive the adoption of data security platforms.
Trend 6
Growing cloud workloads demand data security posture management
DSPM involves proactive monitoring and evaluation of cloud workloads to uphold best practices and compliance standards. The cloud shift drives demand for customized security solutions. Organizations recognize the need for real-time visibility, potential vulnerability identification, and prompt security gap address.
Trend 7
Organizations increasingly adopt unified control frameworks to strengthen compliance and optimize costs
Globally, regulatory/compliance landscape evolves, expands, and becomes more stringent, while risk prioritization and cost-benefit analyses grow more complex.
Trend 8
AI/ML and integrated and quantitative approaches help manage third-party risks
Increasing third-party incidents, a growing threat landscape (especially post-pandemic), and the ever-changing supply chain environment necessitate monitoring of and adherence to cybersecurity compliance in the supply chain.
Trend 9
A paradigm shift to microservices-based architecture and API security
In an era of Agile work and faster GTM, microservices-based architecture is a game changer. Granular components' bigger attack surface makes them prime targets for hacktivists, as shown by recent attacks on industry giants like Facebook and Twitter.
Trend 10
Safeguarding supply chains against cyber threats
Supply chain security protects the interconnected network of vendors, suppliers, partners, and third-party service providers that contribute to an organization's products or services.
Trend 11
GenAI-powered security operations gain wider acceptance
GenAI is an industry buzzword widely applied for its cognitive capabilities. It employs dataset crawling for model training and responding to human queries, predominantly used by security analysts for investigation and analysis.
Trend 12
Data pipelines for effective cybersecurity
Capturing all essential events during a major cyber incident is crucial for analysts to correlate and assess its impact accurately. In such situations, the volume of generated events may become unpredictable and significantly increase.
Trend 13
IT-OT security convergence gains popularity for unified, rapid protection
As IT and OT merge, treat them equally. Apply IT security controls to OT. Collaborate, don't isolate, IT and OT teams. A skill gap exists between OT and cyber teams. Security teams lack awareness of OT device vulnerabilities and patches.
Trend 14
Organizations embrace zero-trust security in OT/IoT network
Zero-trust principles in OT/IoT networks gain importance in cybersecurity. Old perimeter-centric security isn't enough against advanced threats. With more devices and IT-OT convergence, a proactive and adaptive approach is vital.
Trend 15
Cloud-native application protection platform elevates multicloud security for businesses
Enterprises embrace cloud-native approaches in multicloud platforms such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform(GCP). They use microservices architecture with evolved workloads like containers and serverless to develop scalable cloud-ready applications.
Trend 16
Firms secure hyperautomation to future proof their businesses
Hyperautomation reshapes digital transformation through rapid, scalable, and extensive automation. It brings efficiency and cost benefits but opens an all-new attack surface. Securing hyperautomation employs DevSecOps to identify security loopholes and vulnerabilities at each stage of “dev,” “build,” and “run” in the automated application development or infrastructure provisioning life cycle.
Trend 17
Privacy compliance becomes key to digital transformation
Digital transformation amplifies business processes, products, services, and customer experiences. In this data-driven landscape, privacy is crucial for successful transformation. Safeguarding the personal data of customers, employees, and partners fosters trust, loyalty, and competitive advantage in a regulated market.
Trend 18
Customer trust hinges on robust privacy controls
In today's digital world, customers are increasingly concerned about their privacy. They are more likely to do business with companies that have a strong reputation for protecting data. Additionally, many countries have strict privacy regulations, and businesses that want to operate in these markets must comply with these regulations.
What's New
Latest White Papers, Tech Blogs and View Points

Subscribe
To keep yourself updated on the latest technology and industry trends subscribe to the Infosys Knowledge Institute's publications
Count me in!