Infosys Cybersecurity is an amalgamation of the Cybersecurity strategy that supports our Cybersecurity framework and a strong cyber governance program driven through the Information Security Council.
The strategy is designed to minimize Cybersecurity risks and align to our business goals. It focuses on proactive enablement of business, besides ensuring continual improvement in the compliance posture through effective monitoring and management of cyber events. We believe that an effective security culture would complement our Cybersecurity objectives by reducing enterprise risks. Infosys Cybersecurity program ensures that required controls and processes are implemented, monitored, measured, and improved continuously to mitigate cyber risks across domains.
Infosys is committed to
- Protect the confidentiality, availability, and integrity of information assets from internal and external threats
- Ensure and maintain stakeholders trust and confidence about Cybersecurity
The executive Cybersecurity governing body is in place to direct and steer:
- Alignment of Cybersecurity Strategy and policy with business and IT strategy.
- Value delivery to stakeholders.
- Assurance that Cyber risks are being adequately addressed.

Cybersecurity Strategy and Governance
Infosys Cybersecurity is an amalgamation of Cybersecurity strategy that is aligned to the business goals, supporting Infosys Cybersecurity framework – SEED and a strong cyber governance program that is driven through the information security council.
The high-level objectives of the Cybersecurity program at Infosys are:
- Proactive business security and employee experience
- Continuously improve security posture and compliance
- Effective management of cyber events and,
- Building a security culture
Infosys’ Cybersecurity framework is built basis leading global security standards and frameworks such as the National Institute of Standards Technology (NIST) Cybersecurity framework and ISO 27001 which is structured around the below four key areas:
| S | Security management system Governance tier to lead and manage Cybersecurity program of Infosys. The domains in this tier are governance and management in nature for successful Orchestration of different domains of the Cybersecurity Framework |
| E | Enterprise security layer ‘Defense in depth’ approach to secure information and information assets. The domains in this tier are based on the path followed by Information as it flows through different information layers within the organization |
| E | Evolve and transform Set of domains that we are focusing on to evolve and transform within the Infosys Cybersecurity Framework |
| D | Detect and respond Capability to identify occurrence of a Cybersecurity event, implement appropriate activities to act and restore services impaired due to such Cybersecurity incidents |
The framework also entails a comprehensive Cybersecurity maturity model which helps to ascertain the Cybersecurity maturity as well as benchmark against industry peers on an ongoing basis.
This helps in continued oversight and commitment from the Board and Senior Management on an ongoing basis through the Information Security Council (ISC) and the Cybersecurity sub-committee.
In keeping with the ‘defense in depth’ philosophy, we have deployed several layers of controls to ensure that we keep ours, as well as our clients’ data, secure and thereby always uphold stakeholders’ trust.

Cybersecurity Management and Reporting
The Cybersecurity practices at Infosys have evolved to look beyond compliance. The comprehensive Cybersecurity metrics program has been contributing to the continuous improvement of the existing security practices and in integrating Cybersecurity within the business processes.
Information management, being an essential part of good IT governance, is a cornerstone at Infosys and has helped provide the organization with a robust foundation. There is a concerted effort from top management to our end users as part of the development and implementation process. Additionally, care is taken to ensure that standardized policies or guidelines apply to and are practical for the organization’s culture, business, and operational practices. Cybersecurity requires participation from all spheres of the organization. senior management, information security practitioners, IT professionals, and users have a pivotal role to play in securing the assets of an organization. The success of Cybersecurity can only be achieved by full cooperation at all levels of an organization, both inside and outside and this is what defines the level of commitment here at Infosys.
Infosys has established multiple channels including a dedicated portal, common email ID and a helpdesk number for reporting cybersecurity incidents, ensuring accessibility and prompt response for all employees, contractors, and stakeholders.
Infosys has also developed robust business continuity and contingency plans to ensure operational resilience and security. These plans are meticulously designed to address potential disruptions and safeguard the organization against various threats, including cyber incidents.
As a final level of defense, we undergo internal audits as well as external attestations and audits in a year at an organization level (e.g.: SSAE-18, SOC 1 & SOC 2 Type II, ISO 27001) as well as client account audits to assess our security posture and compliance against our obligations on an ongoing basis.
There was no material Cybersecurity incident reported in fiscal 2025.

Our industry contributions and thought leadership
In this era of rapid technology disruptions and digital transformations, Infosys enables the businesses to embrace innovations and adapt to new technologies. We focus on strengthening cyber resiliency through platform led convergence and consolidation of security capabilities and deliver AI-first service offerings.
We promote cybersecurity through various social media channels such as LinkedIn, Twitter, and YouTube; sharing our point of views, whitepapers, service offerings, articles written by our leaders, their interviews stating various perspectives, and podcasts through our corporate handles providing cybersecurity thought leadership. The topics include impact of evolving technologies such as Gen AI on cybersecurity, cloud security, data privacy and protection, and compliance, etc. In addition to this, we work with analysts such as PAC Group and industry bodies such as Data Security Council of India (DSCI), Information Security Forum (ISF), etc. to create joint thought leadership that is relevant to the industry practitioners. In our efforts to strengthen the cyber awareness across social communities, we also participate in cybersecurity awareness initiatives led by non-profit organizations such as NASSCOM. Further, we publish a technology centric report that provides insights into emerging technology trends and how they can be applied to businesses. It essentially acts as a guide for enterprises looking to navigate the evolving digital landscape and make informed technology decisions based on current trends.
Vulnerability Management
The vulnerability management program at Infosys follows best-in-class industry practices coupled with top-notch processes that have been evolving over the years. Rich experience of deftly managing end-to-end vulnerability life cycle of Infosys Network and the constant hunger to stay abreast of the latest tools, technologies and related market intelligence have acted as a catalyst in fortifying the overall vulnerability management program.
A robust enterprise vulnerability management program builds the foundation for healthy security hygiene of an organization. The following practices have been put in place at Infosys for,
- Real time asset discovery followed by instantaneous identification of vulnerabilities, misconfigurations, and timely remediation
- Automation of vulnerability management, configuration compliance, security assessments and review for assets, applications, network devices, data, and other entities in real time
- Close coupling of detection and remediation processes; auto prioritization to reduce the turnaround time for closure of detected vulnerabilities
- Continuous monitoring of all public facing Infosys sites and assets for immediate detection of vulnerabilities, ports, or services
- Regular penetration testing assessments and production application testing for detection and remediation of vulnerabilities on a real time basis
The vulnerability remediation strategy of Infosys focuses on threat-based prioritization, vulnerability ageing analysis and continuous tracking for timely closure. We have successfully eliminated the ticketing system for vulnerability tracking by establishing a continuous detection and remediation cycle, where the IT teams are enabled and onboarded onto the vulnerability management platform. A Cybersecurity awareness culture is nurtured, and teams are encouraged to proactively remediate the vulnerabilities reported on their assets or applications.
Supply Risk Management
A comprehensive supplier security risk management program at Infosys ensures effective management of potential security risks across the various stages of supplier engagement. The process comprises of,
- Categorization of the suppliers based on the nature of the services provided and the sensitivity of the data involved.
- Defining standardized set of information security controls as applicable to each category of supplier
- Defining, maintaining, and amending relevant security clauses in the supplier contracts as applicable to each category of supplier
- Due diligence, security risk assessment for effective management of the information security risks associated with suppliers
Defining and monitoring of key security metrics for suppliers (e.g., background check, security awareness training completion, timely interventions with regard to information security incidents etc.) threat intel tracking and governance further strengthens the Infosys supplier security risk management program.
Cybersecurity Competency Development
With the increasing demand for Cybersecurity jobs and a skilled workforce, Infosys has taken several measures to counter the Cybersecurity talent shortage as well as in skilling, retaining, and diversifying its Security workforce in areas such as application Security / Secure development lifecycle.
Cybersecurity team members undergo technical as well as behavioral trainings on an ongoing basis. Infosys leverages internal training programs, as well as external bodies / agencies with Cybersecurity subject matter expertise, with a strong focus on learning through the classroom as well as on-the-job trainings.
- Over 2400 professionals were trained & 1900 certified across various Cybersecurity domains. These training programs comprises of advanced partner programs from OEM, external agencies and internal Cybersecurity training facility.
- Over 1400 professionals have been trained in AI and other new age technologies.
- Launch of Cyber Aspire Program, as part of which various professionals are trained in niche Cybersecurity domains. Along with this, structured curriculum for freshers and various bridge programs have been launched for upskilling and cross-skilling of cyber professionals.
- Infosys continues its partnership with NIIT to have its professionals undergo a Cybersecurity Master’s Program.
Nurturing, and Upholding, a Robust and Sustainable Cybersecurity Culture
At Infosys, driving a positive and sustainable Cybersecurity culture is one of the key constituents of our robust Cybersecurity strategy. We embrace top-notch tools and technology to strengthen our Cybersecurity stance and have an equally razor-sharp focus to bolster people security and keep fostering a security-first mindset among Infoscions. Various measures are in place to nurture a confident and empowered Cybersecurity culture. At Infosys, we embrace the Secure by Design (SbD) principles at an organizational level with a focused SbD campaign running org-wide, and multiple trainings offered to drive awareness on SecureSDLC. There are various other diverse and proactive communication campaigns driven across the organization via different awareness means / tools, including – posters, cyber comics, employee handbook, caselets, cyber security scorecard, newsletter, advisories, emailers, push messages, annual mandatory awareness quiz, gamification, SME Cyber Talks, information security courses on the internal training platform, sessions, videos, podcasts, fireside chats, blogs, panel discussions, focused social engineering awareness, thought leadership messages, annual flagship event -celebrating the cybersecurity week etc. There is also a video-based, animated, and interactive e-Learning certification program that helps drive positive security behavior amongst the Infoscions.
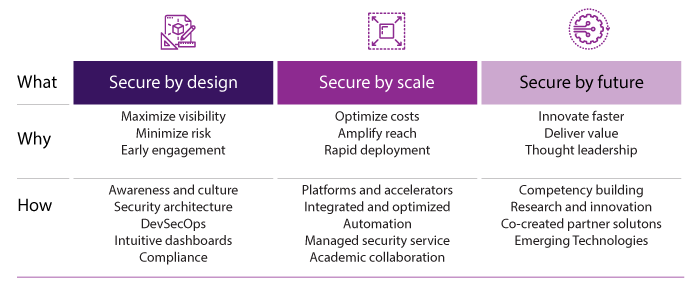
Innovations for our clients
Infosys innovation-led offerings and capabilities:
Infosys Cyber AI, powered by Infosys Topaz, helps customers amplify their defender potential, build effective cyber defenses and enable accurate decision making by leveraging platform-centric Gen AI capabilities. We help enterprises Renew, Re-Architect and Re-imagine their entire cyber strategy through AI with a focus on risk resilience. This helps us become a trusted cybersecurity partner for enterprise customers.
Cyber Next platform powered Services help customers stay ahead of threat actors and proactively protect them from security risks. Our pre-engineered packaged and managed security services help monitor, detract and respond by getting extensive visibility and actionable insight through threat intelligence and threat hunting. Our offerings ensure risk-based vulnerability management by providing a comprehensive single pane of glass posture view. We have made huge progress in the Cyber Next platform powered service delivery through various modules - Cyber Watch, Cyber Intel, Cyber Hunt, Cyber Scan, Cyber Gaze, Cyber Compass, Cyber Central that ensure comprehensive Managed Protection Detection and Response (MPDR) for our global customers.
Zero Trust Security architecture and solutions to navigate our customers to embrace zero trust security. Key innovation and offerings include Secure Access Service Edge (SASE) delivered as-a service. With SASE as-a Service, we ensure strengthened overall security through cloud delivered security controls and capabilities. Infosys innovation in policy standardization enforce controls at access level, accelerate rollout of service thereby reducing or eliminating legacy tools allowing our customers to reduce overall costs while enhancing end-user experience.
Secure Cloud transformation with Cobalt assets drive accelerated cloud adoption. With Secure Cloud reference architecture and Secure by Design principle we ensure security is embedded as part of cloud strategy, design, implementation, operations and automation.
Industry recognition
- Analyst recognition: Positioned as a Leader in the ISG Provider Lens™ Cybersecurity Services and Solutions (2021, 2022, 2023, 2024)
- Analyst recognition: Positioned as a Leader in the Nelson Hall Cyber Resiliency Services NEAT Assessment 2023
- Analyst recognition: Positioned as a Leader in Everest PEAK Matrix® Assessment Identity and Access Management (IAM) Services 2023
- Analyst recognition: Received the ISG Provider Lens Award 2024 for our domain expertise and presence in the Americas, UK and Germany markets
- Analyst Testimonial: “Infosys’ CyberSecurity Capabilities are a Testament to their Relentless Pursuit of Excellence,” says Gautam Sampath, Principal Security Analyst at Information Services Group (ISG)
- Analyst Testimonial: “Infosys' CyberSecurity Portfolio is a Strong Choice,” says Gautam Sampath, Principal Security Analyst at Information Services Group (ISG)
- Client testimonial – Strengthening Cybersecurity: BECU leaders’ insights on the impact of Infosys Collaboration
- Client testimonial – Cummins and Infosys: Securing Identities Together
- Client testimonial – Infosys provides Managed Protection, Detection and Response to bpost (Belgian Post Group)
- Client testimonial - Infosys secures MS Amlin's digital transformation journey
- Client testimonial – Infosys and Ferroglobe: Journey towards a robust and secure cyber landscape
- Client testimonial – Ferroglobe partners with Infosys to secure their OT Security Environment
- Partner award: Received the Saviynt APJ Regional Delivery Partner of the Year 2024 for our innovation and excellence in leveraging Saviynt’s Identity Cloud to solve complex identity security challenges.
- Partner award: Received the Zscaler GSI Growth Partner of the Year 2024 award for our unwavering commitment to delivering exceptional business outcomes and enhancing Zero Trust implementation
- Partner award: Acknowledged as the Microsoft Security Solutions Partner across all 4 domains demonstrating our cutting-edge expertise in deploying Microsoft Security solutions
- Partner award: Acknowledged as the AWS Competency Partner across seven domains exhibiting our in-depth technical expertise in AWS security and delivering tailored, security-focused solutions for specific workloads and use cases

