Success Stories
Strengthening operational resilience with integrated security platforms across OT landscapes
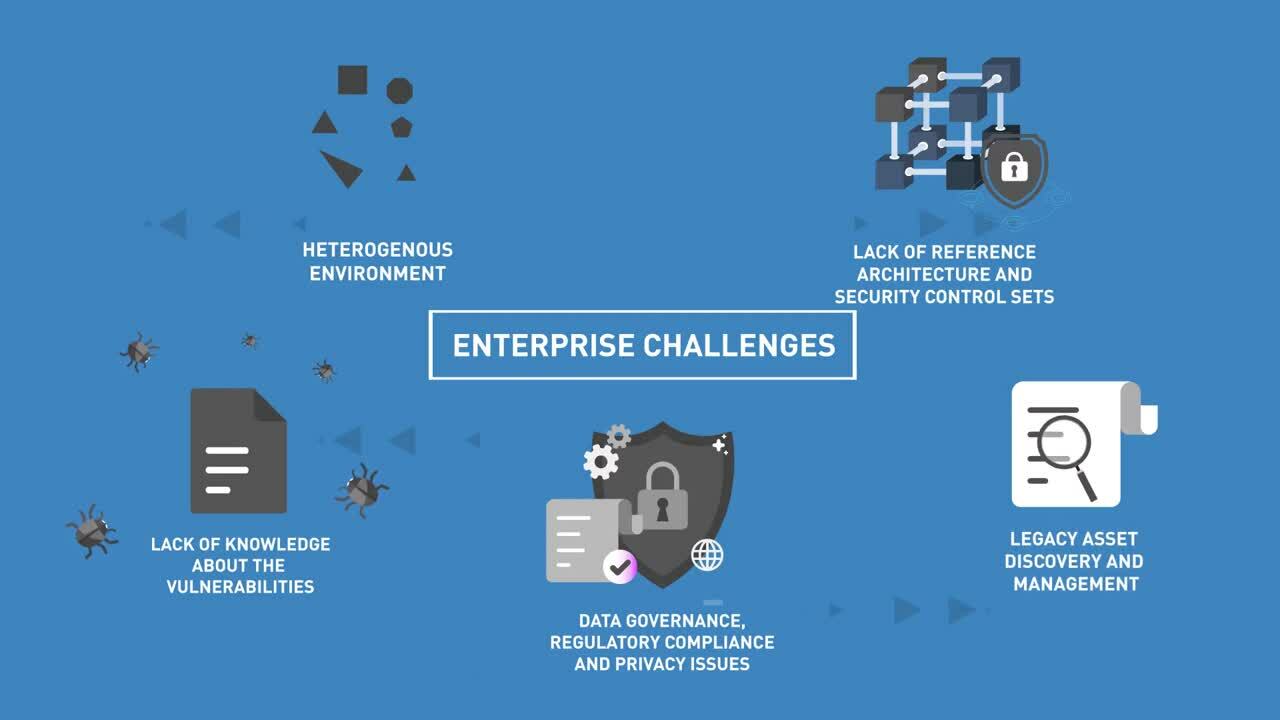
The convergence of IT and OT systems makes Operational Technology (OT) a prime target for cyberattacks, with AI-powered threats exploiting vulnerabilities and causing widespread disruptions in critical infrastructure. OT's complexity, coupled with IIoT and legacy systems, significantly expands the attack surface, risking safety, environment, operations, reputation, and finances. This necessitates robust OT security, aligned with industry standards and regulations across various segments, private enterprises, and government sectors to safeguard critical infrastructure and ensure business continuity.
Infosys's OT Security solutions, powered by Cyber AI NextGen SOC and Infosys Topaz, address these unique challenges. They provide enhanced visibility, proactive vulnerability mitigation, improved operational resilience, and effective cyber incident response. Prioritizing OT security is essential for maintaining safety and environmental protection, safeguarding assets, ensuring operational efficiency, and mitigating public safety risks in today's evolving threat landscape.
Discover our approach to securing Operational Technology (OT) Assets across industry segments
Driving innovation and enhancing security for critical infrastructure through our Operational Technology (OT) security solutions
Infosys enables seamless IT/OT convergence while preserving system integrity, availability, and security. Through network segmentation, zoning, and secure architecture design, we reduce the OT attack surface and limit lateral threat movement - fortifying critical infrastructure against evolving cyber threats.
Harnessing AI-driven analytics and real-time monitoring, Infosys empowers organizations to detect, analyze, and respond to threats across ICS and XIoT environments. This proactive approach ensures continuous visibility of industrial operations and rapid incident response, minimizing downtime and safeguarding operations.
We help clients build resilient OT Security governance models aligned with global standards such as NIST 800-82, ISA/IEC 62443, NIS2, and NERC-CIP. Our structured frameworks and automated compliance solutions are compliant with industry standards and regulations and seamlessly integrate OT security roadmaps with broader business objectives.
Strengthening operational resilience with integrated security platforms across OT landscapes
Our comprehensive risk assessment services leverage state-of-the-art tools and unparalleled expertise to pinpoint vulnerabilities within the industrial control systems (ICS). With meticulously crafted recommendations, strategies, and roadmaps, we empower organizations to fortify defenses and ensure uninterrupted operations.
Our comprehensive risk assessments extend beyond evaluation to encompass meticulous plant network topology design and blueprint deployment. We seamlessly integrate cutting-edge OT security platforms, fine-tune and optimize them to minimize false positives and enable plant engineers to prioritize genuine threats. Our expert OT security engineering services facilitate seamless integration with third-party solutions, to create a robust and cohesive security posture.
Our fortified assessment framework, powered with cutting-edge tools, aligns seamlessly with industry benchmarks such as NIST and ISA 62443, ensuring compliance with NIS2.0, NERC-CIP, and other regulatory mandates. Our tool-based approach empowers deep visibility into organizations’ OT environment, elevating its security posture. Additionally, Infosys meticulously maps regulatory requirements against organization’s existing control framework, providing a comprehensive gap analysis to bridge the disparity between the current state and regulatory mandates.
Our comprehensive service extends beyond mere discovery to pinpoint critical assets, often elusive within complex OT environments. By establishing a robust baseline and conducting meticulous risk analysis and prioritization, we empower organizations to proactively address vulnerabilities. We offer a holistic vulnerability management lifecycle, encompassing discovery, risk assessment, and governance, ensuring the security of critical infrastructure.
Our comprehensive service safeguards OT environments against an ever-evolving spectrum of threats originating from within or beyond its perimeters. We deliver round-the-clock security monitoring and triaging, coupled with unwavering incidents and alert management, seamlessly integrating with the existing SIEM/SOC infrastructure. Our continuous security assessment and remediation ensures the resilience of critical assets.
Our innovative Cyber Next platform empowers seamless integration of OT and IT security operations, eliminating the need for redundant SIEM/SOC deployments. By leveraging OT-specific solutions for log and event collection, we aggregate data within our Managed Security Services (MSS) Cyber Next platform, enabling swift incident response and sophisticated threat analysis.
Our comprehensive approach extends beyond the initial design and implementation, seamlessly blending administration and management of ongoing security operations. By providing continuous support and service, we ensure the smooth and secure functioning of critical infrastructures, empowering organizations to focus on their core objectives while we handle the complexities of operational security.
Zero Trust OT Security is a modern cybersecurity framework designed to secure OT infrastructure by enforcing strict access controls, authentication, micro-segmentation. Further, with the rise of remote access and potential lateral movement of threats, securing remote connectivity is critical. We provide comprehensive solutions based on Zero Trust principle, encompassing design, implementation, and ongoing management. This approach ensures that every access request is meticulously authenticated, authorized, and monitored, empowering organizations to securely enable remote work while minimizing potential risks.